Learn more about the Goals Module and its key monitoring and reporting features.


With its recent opening this past summer, this private data facility provides a state-of-the-art construct merging leading-edge technology, hardware solutions, and computing software to deliver a scalable, secure, multi-tenant, private internet-based service.
Contemporary choices in scalability, performance, availability, recovery, and compliance can provide unrivaled application reliability.
A new industry trend, called hyperconvergence, combines computing, storage, and networking into one compact, manageable device or “node.” Leveraging this type of infrastructure enables us to scale dynamically without having to procure and connect each capability separately - and at a significantly better cost point.
In short, it means we can more easily scale as you scale.
Our computing environment is fully virtualized, allowing us to dynamically add processing power or memory to support changing application needs. When needed, we can quickly redefine the environment in software without complex and costly physical configurations.
Redundancy is built into each layer of the environment, with no single point of failure. This ensures the highest levels of application availability - over 99.9% uptime - so users can always access their data.
When unavoidable disaster strikes, a fast and reliable way to recover - or fail over - is to have another processing location as a back up. This geographically diverse secondary private data center continuously replicates the systems and data from our primary production environment, providing industry-leading recovery times and an always-on solution.
A Tier 4 class data center meets industry SSAE 18 standards for operational processes, security, redundancy and availability. Asurity also holds application development, delivery, and support processes to equally high standards, ensuring ongoing compliance with annual SOC audits.
As the financial industry continues to face complex and evolving security threats, Internet-based software solutions like those at Asurity provide peace-of-mind, costs savings, and space to grow quickly without forgoing hi-tech innovations and best-in-class data security. Meeting today’s information security challenges, and ensuring data is housed in bullet-proof - or hack-proof – environments, is best served by a multi-pronged approach.
Asurity’s approach to information security is to build it from the inside out. Taking a layered approach to information security is critically important to meeting the security requirements of every institution we serve - big and small.
While everything is maintained within one data center, each customer is completely isolated and secured away from other customers, work fronts, and applications.
All stored customer data is encrypted in transit and at rest, to protect against attempted data theft. In industry jargon, we safeguard our encryption keys using tamper-proof FIPS 140-2 compliant key management systems.
Asurity software is developed following rigorous secure coding standards, and routinely undergoes secure penetration testing and ethical hacking to identify and eliminate potential weaknesses. We simply won’t deploy software that doesn’t pass this level of testing, so you can be confident that our systems are always secure.
Our web application firewalls, including intrusion prevention and detection capabilities, digitally inspect every packet of data for potential threats. Active vulnerability scanning ensures we stay up-to-date with virus and malware protection.
Proactive security monitoring provides assurance that all security alerts, no matter how insignificant, are being reviewed, 24-by-7. Our security operations center staff can take swift action to keep hackers out and your data safe.
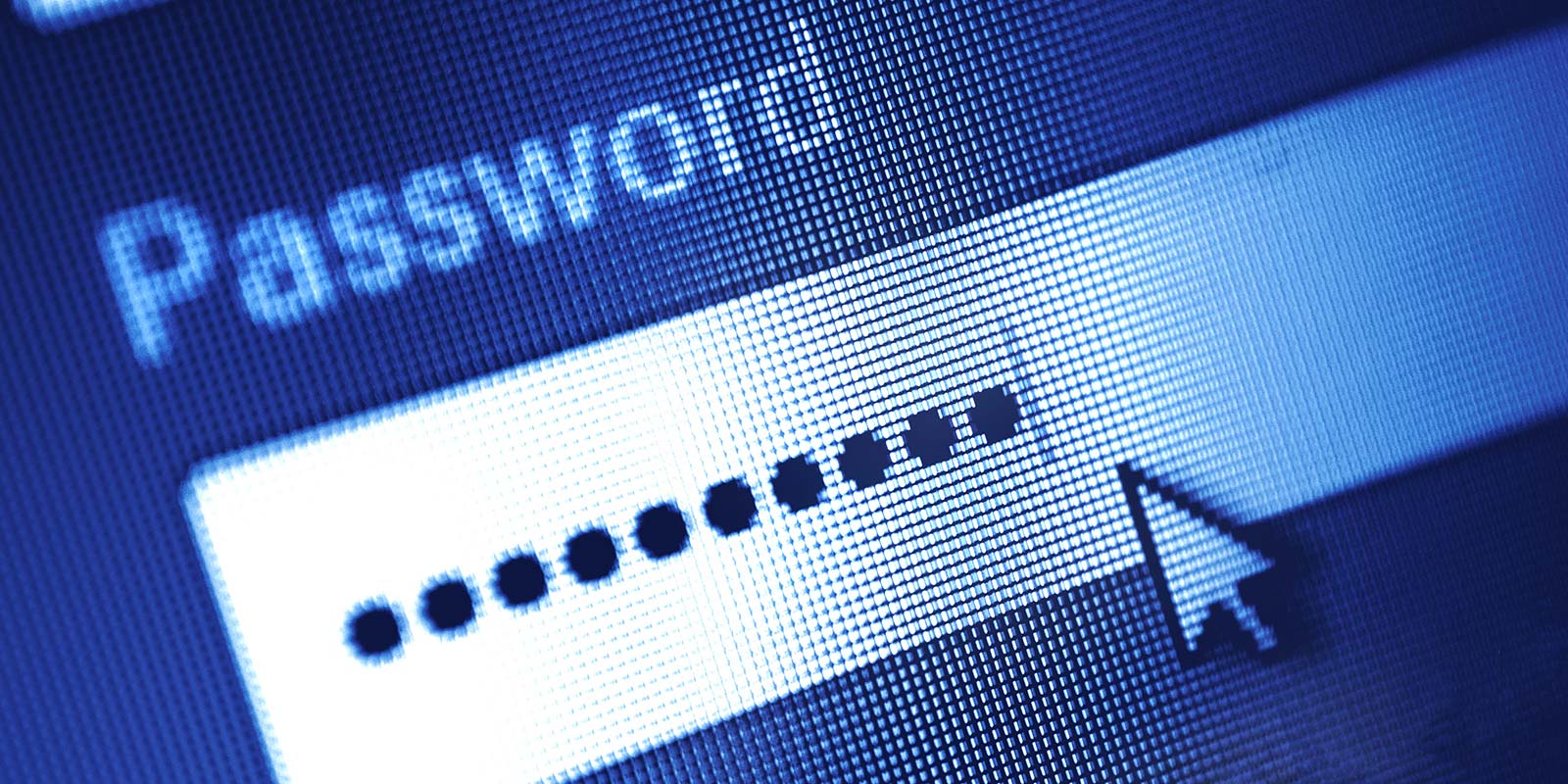
All Asurity applications employ multiple levels of authentication as well as distinct user roles to ensure that authorized users are allowed to access only what they need.
This new environment was built in anticipation of the evolving infrastructure and data security requirements of the financial services industry. The solutions at Asurity are prepared to keep your data safe, secure, and always there when you need it.
Welcome to our future.

Learn more about the Goals Module and its key monitoring and reporting features.
Learn about the changes of state consumer protection and the responsibility of financial services institutions to pursue operational excellence and a culture of compliance.
Regulatory and technology experts discuss innovation, CRA reforms, and how single-close construction loans are reenergizing rural America.